Demonstration of the right way to abuse the shortage of trusted visible path and HTTPS to steal customers Apple credentials.
source
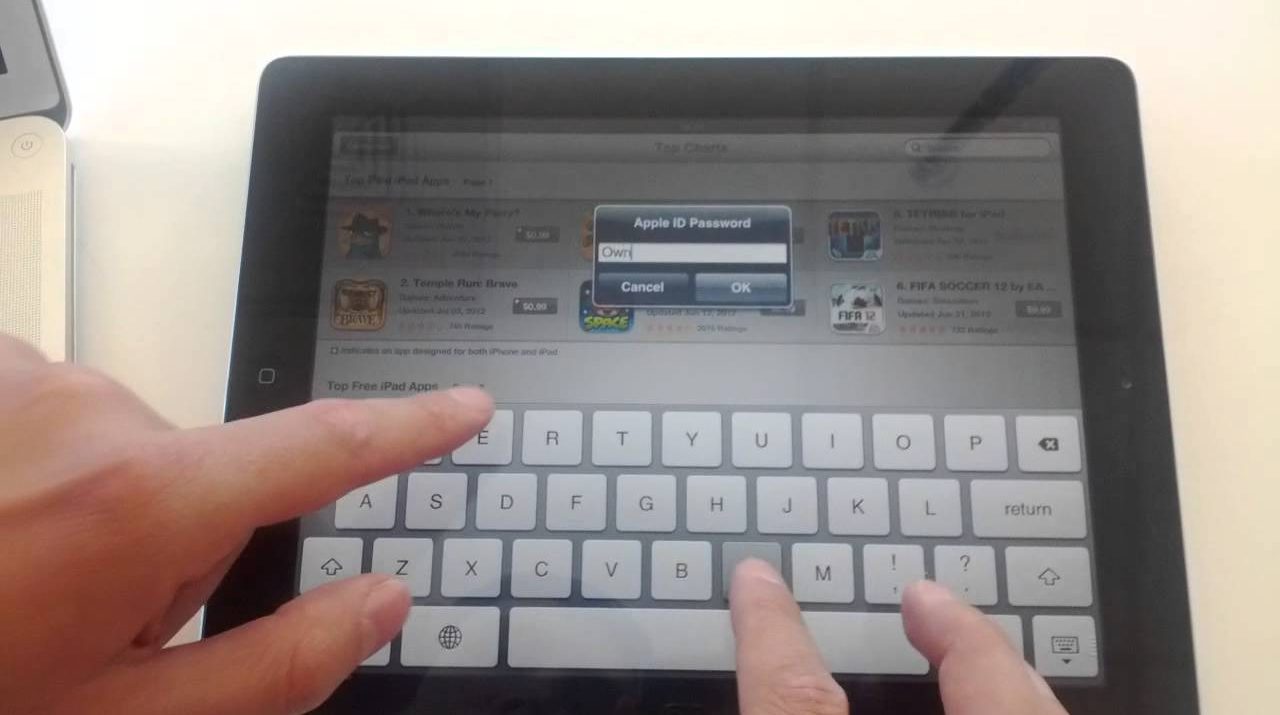

Demonstration of the right way to abuse the shortage of trusted visible path and HTTPS to steal customers Apple credentials.
source